Pivot To True Security
Defining Global Standards for Quality, Trust, and Excellence in Data Security Across Every Industry
01
Skilled red team conducts realistic attacks to expose vulnerabilities, advising on strengthening defenses and safeguarding assets against evolving threats.
02
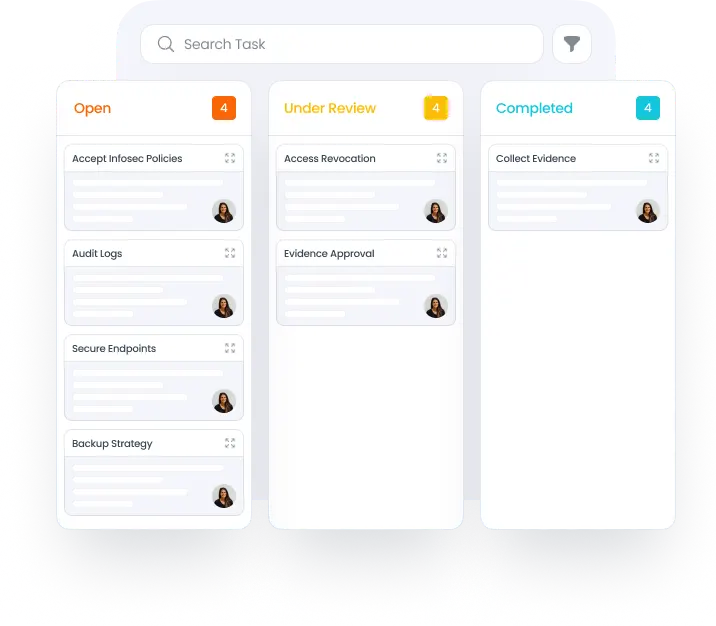
Building a collaborative workspace for internal stakeholders, security team, consultants, and auditors.
03
Simplifying manual evidence collection so that your team can focus on improving your security posture rather than documenting it.
04
Democratizing the security responsibility across the organization to eliminate the need for constant follow-ups for evidence.
05
Managing and sustaining your compliance and security posture over time.
06
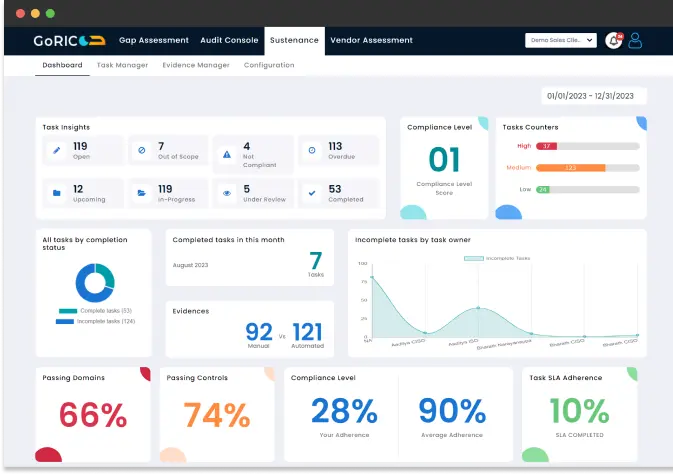
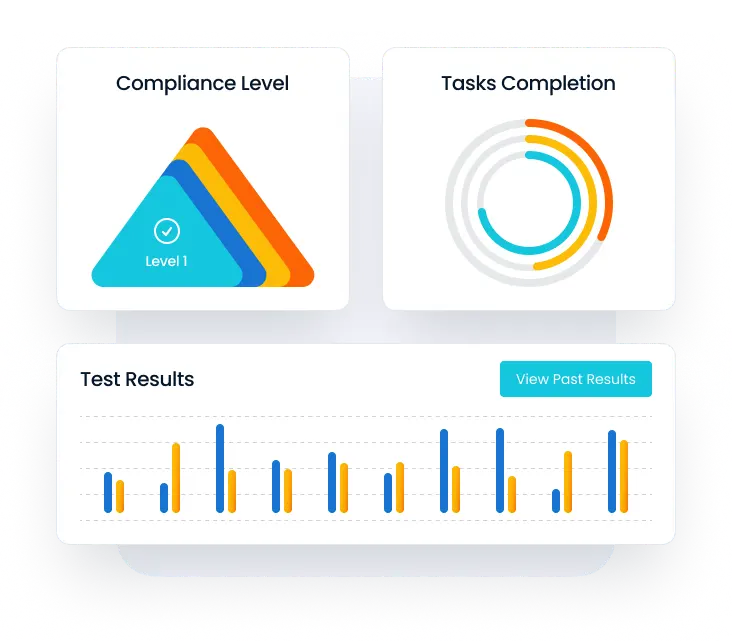
Accessing real-time security posture score anytime for an accurate assessment.
GoRICO Is Here To Simplify Your Security Compliance Journey
Here’s Why
Customized to Your Company’s Requirements
- Tailored for cloud-native, hybrid, and on-premises environments
- No two companies are the same, so why should your GRC be? 100% custom workspace designed for you, your team, technology, and security stack
- Leverage your existing policies, procedures, and security investment to streamline and enhance your governance, risk, and compliance processes
Average 125 Hours Saved Per Month
- Enable clients to assess their true security posture by providing access to real-time compliance and security scores
- Allow task owners to easily identify and address the actions needs to meet your security benchmarks
True Security Posture
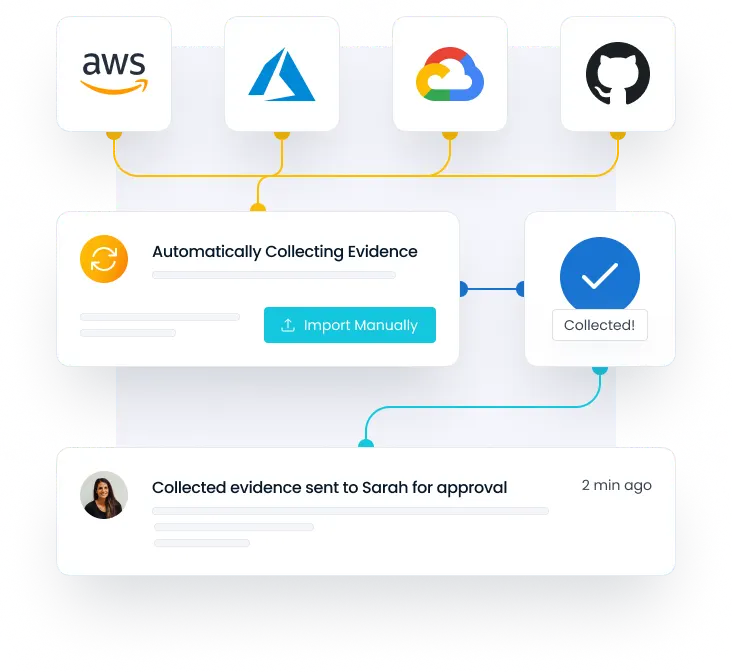
- Automated evidence collection
- Quicker manual evidence collection
- 10x faster evidence collection with smart delegation and tracking
- 50% to 100% faster manual and automated evidence collection
Audit-Ready Always
- Year-long evidence collection across stakeholders
- Automatically enriched audit console with evidence based on the testing period and framework
- Collaborative workspace for auditors and internal security teams
Most Popular GoRICO Features
Efficient cross-mapping for rapid security credential attainment across all compliance frameworks
Cater to clients with various setups, including cloud-native, hybrid, or on-premises environments
Enhance efficiency through automated task delegation
Fosters smooth communication among stakeholders with a collaborative workspace
Tailor policies and procedures to meet specific needs
Automated evidence collection from third-party technologies
Quick manual evidence collection
Tracks progress effortlessly with posture and compliance scores, identifying areas for improvement
Make Your Security Compliance Easier