Article
GoRICO: The TPRM Tool for Third-party Vendor Assessment
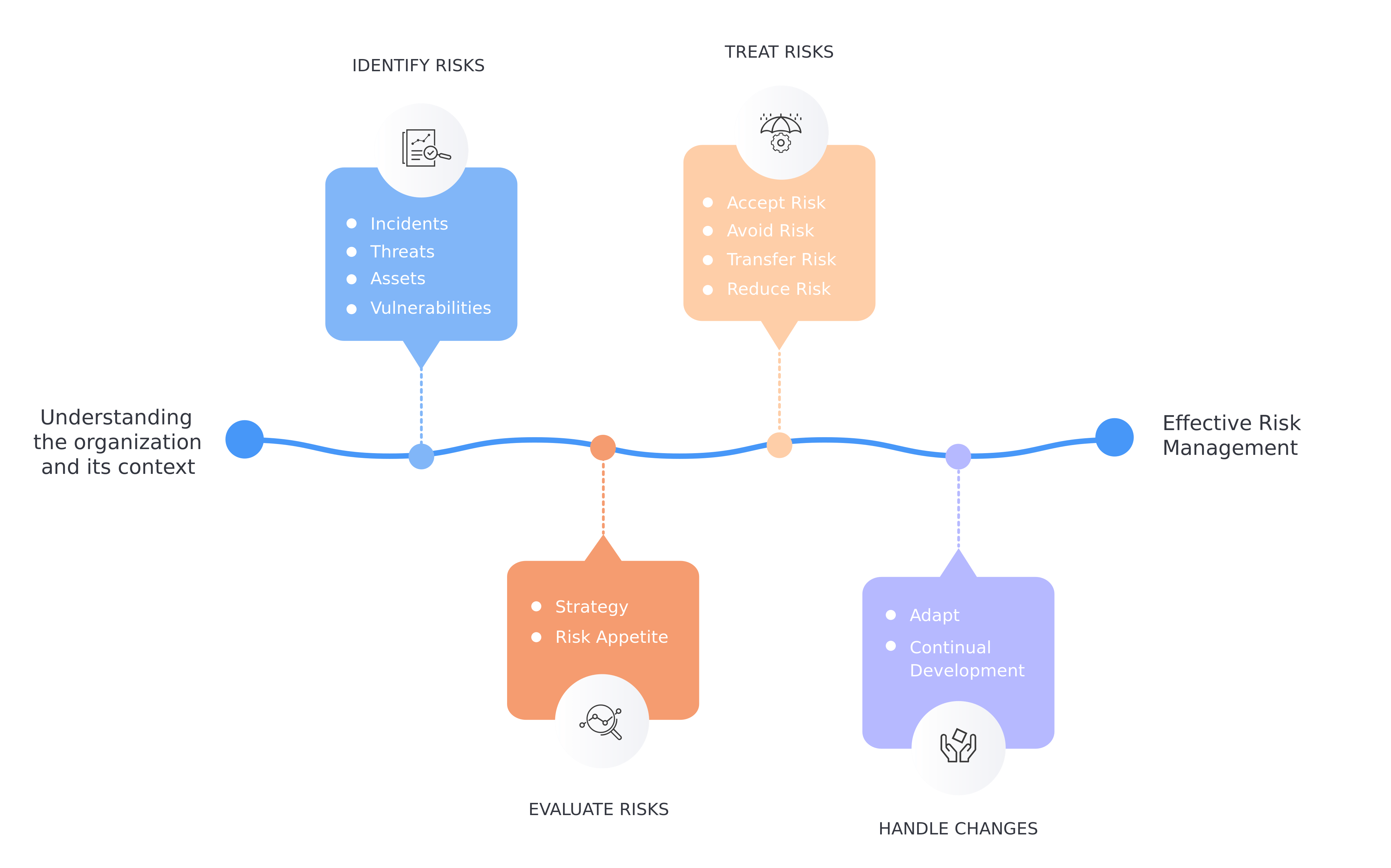
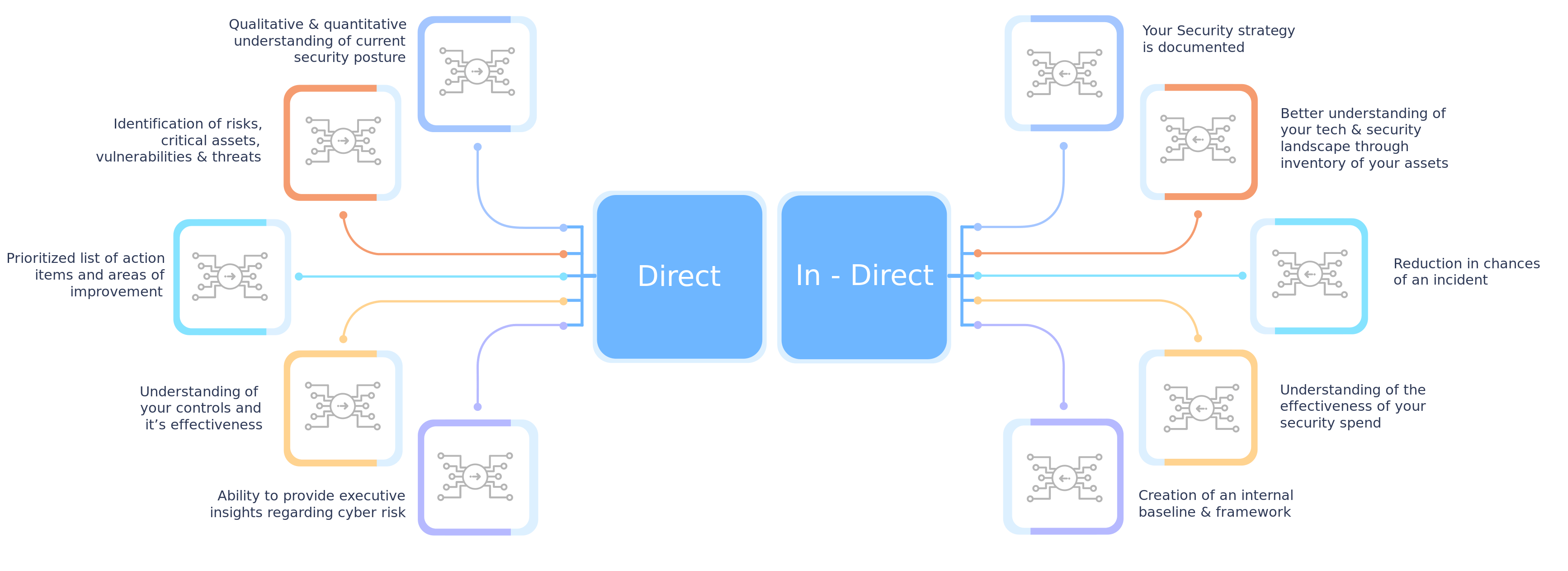
With the advancement of technology, an organization’s reliance on third-party vendors to keep operations running has increased exponentially. However, increased dependence results in increased information sharing which comes with its own set of risks. According to Verizon Data Breach Investigations Report (2023), 83% of breaches involved external parties and, TPRM (Third Party Risk Management) still continue to be one of the top five challenges CISOs face in 2024 due to ignorant Third-party Risk Management practices. What are Vendor Risk Assessment Questionnaires in TPRM? Vendor risk assessment questionnaires are among the most popular methods for managing third-party vendors. These questionnaires provide an understanding of the vendor’s security posture and identify existing or potential vulnerabilities that can lead to a data breach. These are vital to TPRM, especially when the vendor is handling a critical business function. A good vendor risk assessment questionnaire includes understanding the vendor profile, background, compliance with regulations, standards, data management, privacy practices, third-party audits, certifications, incident response, recovery plan, access control, and ongoing monitoring. However, managing the vendor risk assessment of hundreds or thousands of vendors on spreadsheets can be tedious and not the most efficient solution. In such instances, using a tool, such as GoRICO, that can perform this task comprehensively is a more streamlined, systematic, and effective route. Streamline Vendor Assessments with Accorian TPRM, offered by Accorian, as part of its security consulting services helps reduce financial risk, enhance data security, safeguard reputation, and mitigate regulatory risks. It also includes risk identification and comprehensive vendor risk assessment via a vendor questionnaire. Why GoRICO? GoRICO, the governance, risk, and compliance tool, which has been developed inhouse, is a unified platform solution designed to comprehend, fortify, and oversee modern technology-driven enterprises' accurate security posture, including the vendor risk assessment module. GoRICO’s vendor risk assessment module includes features like customizable questions, risk and criticality-based vendor profiling, end-to-end assessment tracking, automated workflow, evidence-based assessment, and comprehensive insights, which ensures thorough and effortless engagement with vendors. Vendor Risk Management Inheriting risk comes with every new vendor relationship. It refers to the risks the vendor poses to the organization at the beginning of a business relationship, which can be related to the nature of the services provided or the third-party vendor's information security posture. Hence, it is important to categorize vendors based on inherent risk. GoRICO segregates vendors into critical major, critical minor, or non-critical. A supplier involved in operations, protecting sensitive data, and publishing certifications on its website is a critical major, while a supplier engaged in operations and protecting sensitive data is a critical minor. A supplier who does not have access to critical or sensitive information and does not pose a threat is non-critical. GoRICO simultaneously oversees the evaluations of multiple vendors; the vendor risk management panel monitors the list of vendors, criticality, contact information for the person in charge, date, status, and action. Vendor Questionnaire GoRICO offers customized assessments for vendors, covering domains like attestations, network protection, password management, access control, BCP/DR, and data governance. The assessment manager records vendor evaluation trigger dates, expiration dates, status, and completion scores. Vendors and assessors communicate via notes. The auditor evaluates vendor assessments based on the evidence and GoRICO’s evidence manager plays a pivotal role in this, as it is responsible for maintaining and collecting the evidence shared by the vendors while ensuring the integrity of the assessment process. Post-evaluation, the status of the assessments changes to approved, failed, or returned. Vendor Risk Management Dashboard GoRICO’s dashboard provides a graphical representation of the assessment results. It highlights the metrics for a combination of multiple vendors, such as the number of...
View More