Everything you need to know about getting your SOC 2
Written by Om Hazela
Accorian has aided 100s of companies in attaining SOC 2 compliance through its end-to-end implementation services. Subsequently, our audit arm – Accorian Assurance, has enabled independently conducted audits and attestations to provide clients with their SOC 2 reports.
In the last few years, SOC 2 reports , have become the de facto way for service providers, especially SaaS companies, to showcase security assurance to their clients. Hence, it’s essential for companies that transmit, process, or, store client data. All SOC 2 reports contain a 3rd party auditors (CPA) opinion on the end company’s security posture against the requirements of the reporting standard (auditing procedure) along with scope information, exceptions, and deviations.
Such a report will aid in taking the cybersecurity question off the table by showcasing a level of security assurance to your clients and simplifying vendor evaluations & security due-diligence checks. Thus, allowing you to focus on the growth of your organization.
IS SOC 2 AN AUDITING PROCEDURE
SOC 2 is a reporting framework and auditing procedure, and not a set of hard rules. It’s a set of best practices across various security attributes and domains with strong signals, that an organization needs to prioritize, encasing the criteria of Security, Availability, Processing Integrity, Confidentiality, and Privacy. These went on to formulate the TSCs (Trust Service Criteria) for SOC 2.
We would like to reiterate that a SOC 2 report does not prove that an organization is 100% secure, but, it’s a great baseline & starting point in your journey to instill security assurance and trust in your customers.
HOW DOES SOC 2 AID MODERN ORGANIZATIONS
Today’s modern organizations, especially service providers, need to showcase security assurance through attestations/certifications across various global, regional, and industry-focused security frameworks like ISO 27001, HIPAA, HITRUST, GDPR, CCPA, NIST CSF, etc.
Breaking down AICPA’s suite of SOC Reports
Soc stands for ‘System and Organization Controls.’” These were formerly called Service Organization Control reports. SOC is a suite of reports from the AICPA that CPA firms can issue in connection with system-level controls at a service organization.
SOC 1 – Report of your internal controls related to financial data & statements
SOC 2 – Report of your internal controls related to the 5 TSCs
SOC 3 – Report on the results of SOC 2 for public consumption
What is a SOC 2 Report?
- A SOC 2 (System and Organization Control 2) report is an objective third-party review of an organization’s commitment to service, security, and trustworthiness via a System and Organization Controls (SOC) examination
- A SOC 2 report is a confidential document with the auditor’s attestation. It is shared with end clients by organizations, especially service providers, to showcase assurance through internal controls for security and exceptions (if any). Thus, ensuring client data is secure. Since there are no exhaustive set of requirements, SOC 2 is different from several other information security standards and frameworks
- End organizations are required to engage a SOC 2 auditor (CPA firm with AICPA membership) to review agreed-upon procedures relating to the organization’s internal controls and issue a report thereof.
TSC Examination (Trust Service Criteria)
SOC 2’s TSCs cover five key criteria across security. They are as follows – Security, Availability, Processing Integrity, Confidentiality, and Privacy.

The baseline TSC is Security, and is mandatory for all SOC 2 assessments. Often organizations choose the other TSCs based on the nature of their business and the assurance required to be showcased to clients. However, we would recommend your company be audited across all 5 TSCs to ensure that your organization securely manages client, sensitive & internal data. Thus, protecting the interests of the organization and its clients.
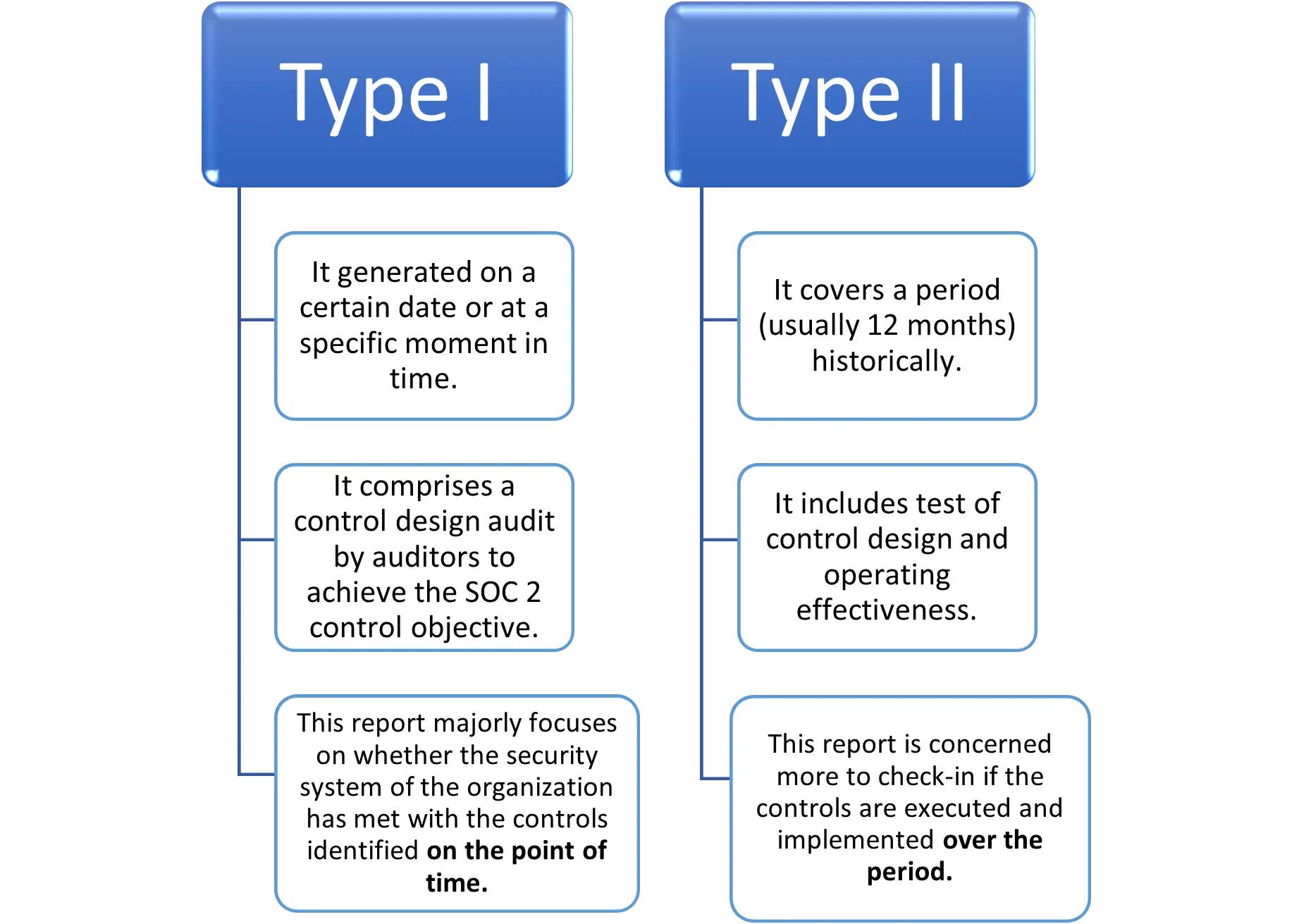
Types of SOC 2 Report:
- A Type 1 report is typically sought after by companies that have a nascent security framework and maturity. For this report, auditors focus on the security framework (Policies, Procedures, and SOPs) and implementation of internal controls. They review the evidence and provide their feedback to capture the current posture against all the clauses. This capture also includes exceptions, deviations, etc.The Type 1 report is a point-in-time assessment and does not assess control maturity. Hence, it’s ideal for companies that have recently implemented their security framework and controls.
- A Type 2 report is ideal for companies who’ve designed, implemented, and achieved a steady state across a significant period of time. The auditor will assess the organization’s security framework and control implementation for maturity across a fixed period of time (the minimum is 6 months).
It is not mandatory to finish a Type 1 audit before a Type 2 audit. But, it is recommended for companies who are implementing security for the first or, have a nascent security posture.
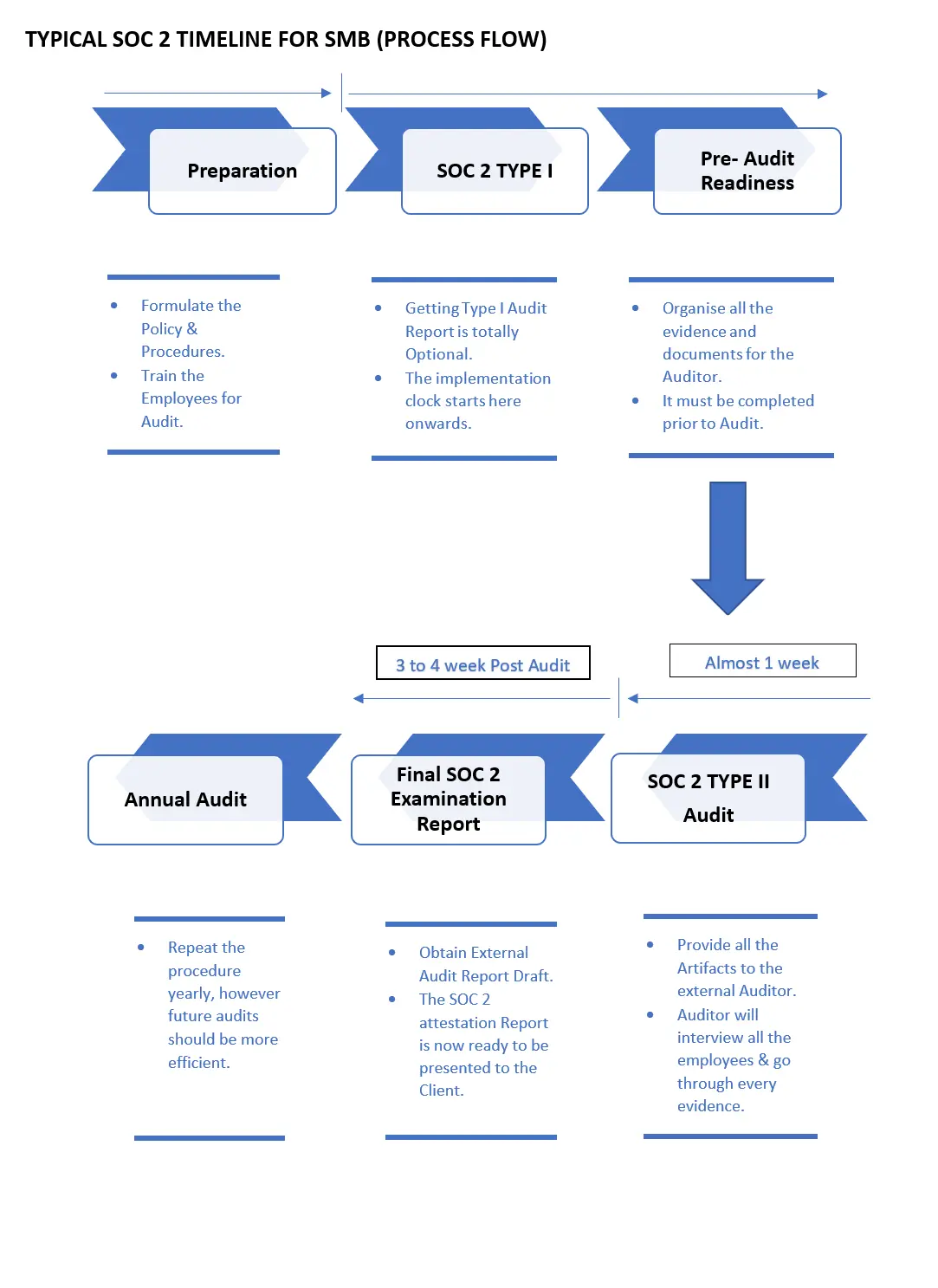
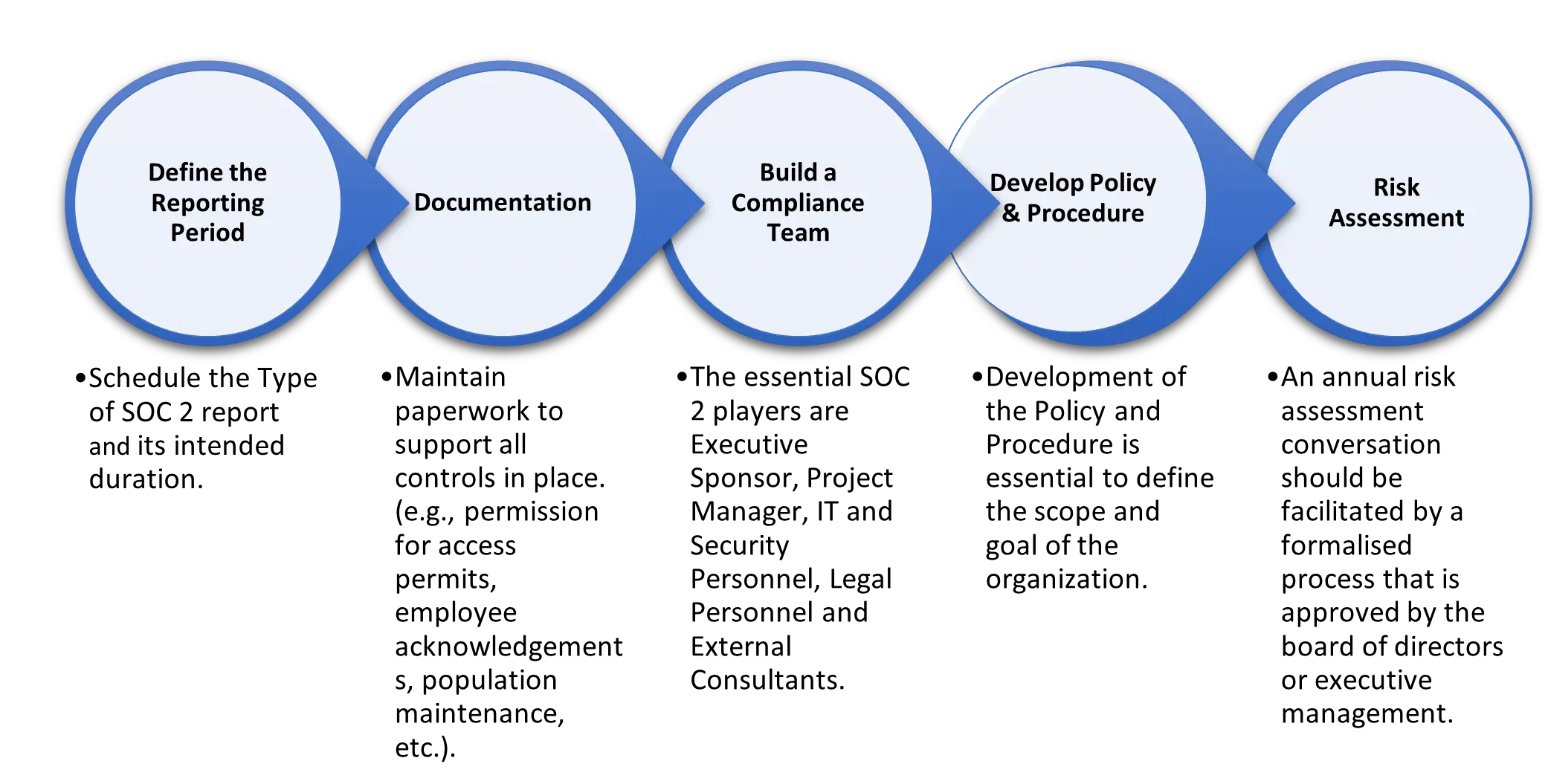
TYPICAL SOC 2 TIMELINE FOR SMB (PROCESS FLOW)
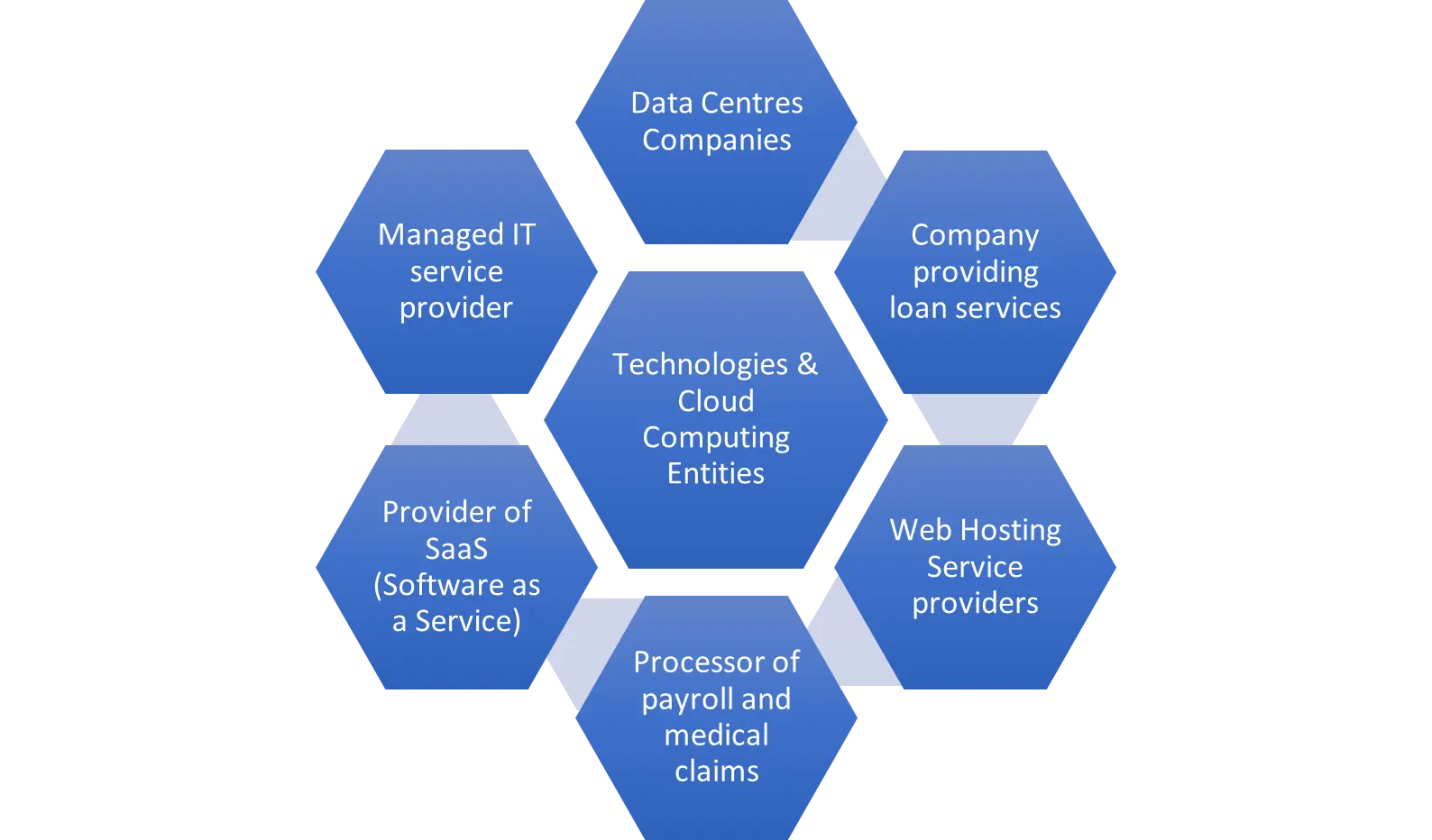
WHO NEEDS A SOC 2 REPORT?
- An organization that offers services or that collects, manages, or transmits client data or, sensitive information is recommended to undergo a SOC 2 audit by an assessor. It can also be used by organizations to assess their current security posture across their security framework, control implementation
- Numerous organizations are eligible for a SOC 2 report, including but not limited to
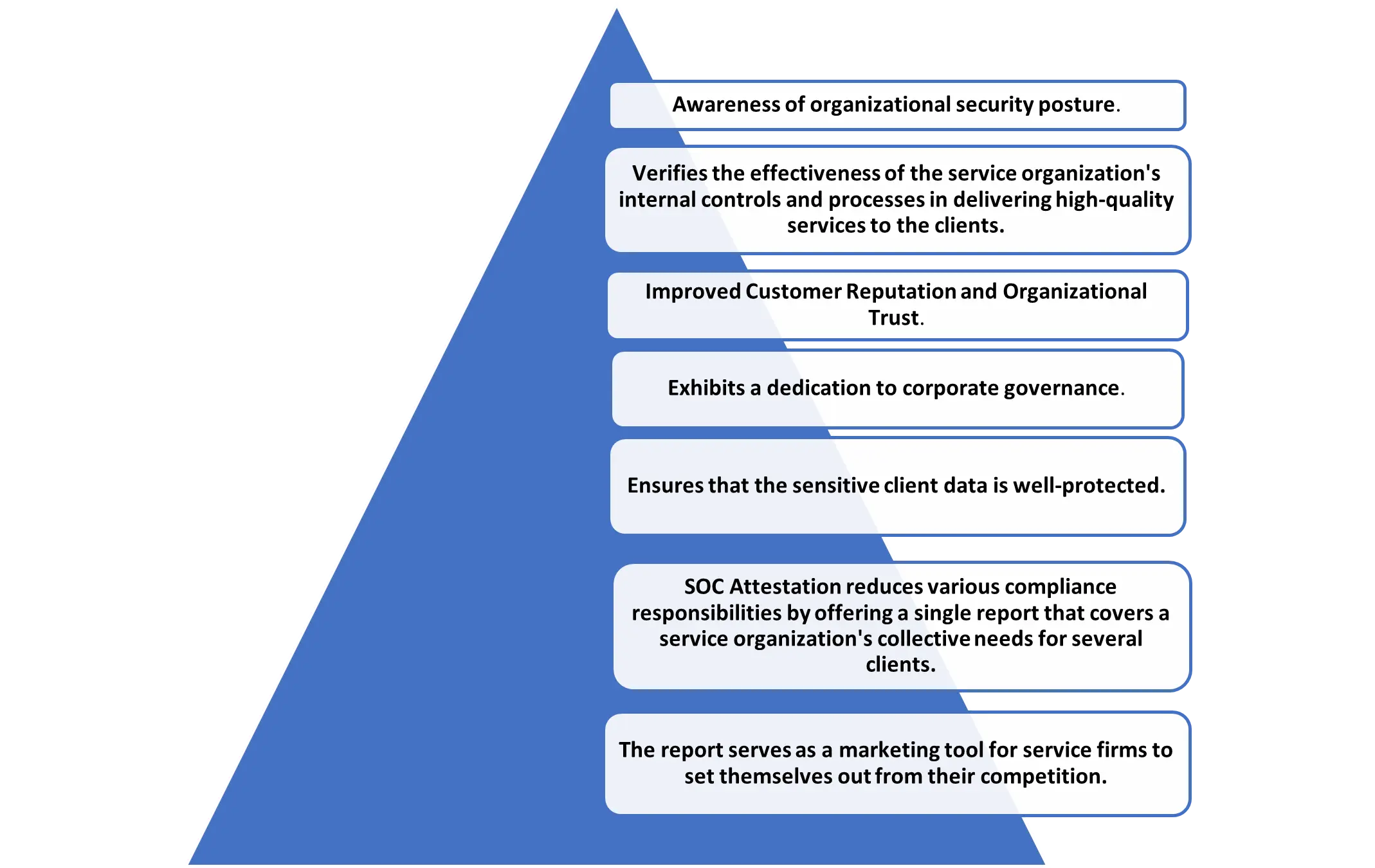
BENEFITS OF SOC 2 EXAMINATION REPORT
Few important benefits are as follows:
PREPARATION FOR SOC 2 & IT’S EXAMINATION:
While the scope of each SOC report varies from client to client, certain areas of focus are common to all SOC examinations. An organization can begin preparing its employees for a better control environment and, as a result, a more efficient SOC inspection by focusing on the following tasks.
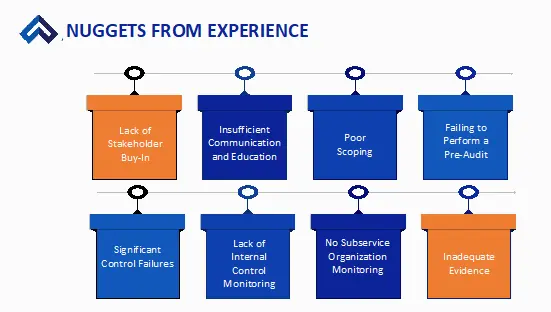
COMMON PITFALLS
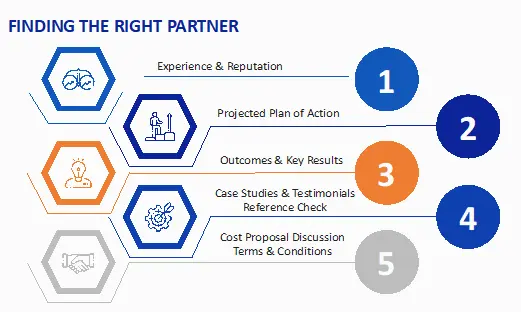
FINDING THE RIGHT PARTNER FOR YOUR SOC 2 JOURNEY
Choose your implementation & remediation advisory partner and, finally the auditor should be based on the following criteria
WHY CHOOSE ACCORIAN FOR SOC 2 EXAMINATION REPORT?
Accorian can aid you in achieving your SOC 2 report from start to finish. This would include:
- Scoping
- Gap Assessment
- Security Framework Development: Writing and updating policies & procedures
- Security Tool Implementation Services
- vSecurity & vCISO Services – Short-term staff augmentation
- Remediation Advisory with validated recommendations
- Pre-audit
- Type 1/Type 2 audits by our independent audit team
- Sustenance services
We specialize in aiding service providers and SaaS companies.
Hence, regardless of where you are in your SOC journey or, your level of security compliance or, security posture, working with a team of experts helps reduce the time required to understand the framework, things to be implemented, and validated recommendations on tools & controls that need to be implemented.


