Article
Manufacturing Sector Vulnerable to RCE Flaw
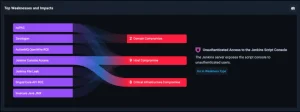
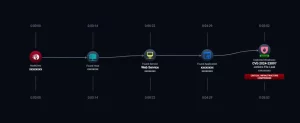
Description PTC, a leading software provider for critical manufacturing organizations, has recently addressed an RCE flaw tracked as CVE-2024-6071. The vulnerability, rated CVSS 10, exists in the PTC Creo Elements/Direct license server. It enables unauthorized remote command execution and lateral movement within critical manufacturing and industrial organizations, including Volvo, Lufthansa, Medtronic, HP, Merck, and GE. Impact The flaw impacted the license server of Creo Elements/Direct, a direct modeling CAD software used for creating 3D designs. Although PTC claims the flaw has not been exploited, its severity prompted immediate patching. Exploitation requires network access, as the license server is typically not exposed to the internet. Affected Versions Thomas Riedmaier discovered a vulnerability in the Creo Elements/Direct license server: Versions 20.7.0.0 and earlier Remediation Apply PTC's patch for Creo Elements/Direct. Confirm that the license server is not exposed to the internet. Limit access to authorized personnel. Isolate license servers from critical systems. Monitor logs for unusual activities. Perform vulnerability scans and penetration tests. Include CVE-2024-6071 in the incident response plan. Stay updated with PTC for new patches or information. Verify security standards meet industry standards and regulations. Source: https://www.databreachtoday.com/patched-rce-flaw-that-affects-critical-manufacturing-a-25699?rf=2024-07-04_ENEWS_SUB_DBT__Slot8_ART25699&mkt_tok=MDUxLVpYSS0yMzcAAAGUHWCLsDa8Alxx89nmcsSkjc0bON4Bwse5npVDdr3B95f5QKt3z4jov6Sh9a9st3fsPv5nXDXDKzV_xxTJ6PXLupMU0TxzCH1TswlToT_AzdymozuPuw Contact us to schedule a scan and discuss your specific security needs. For any further assistance, kindly reach out to us at info@accorian.com
View More