Written by Somya Agrawal II
WebSocket is a powerful tool for sending and receiving messages over a network. It enables quick and reliable data exchange by establishing two-way communication between the server and the client. It is used in everything from online gaming to real-time data streaming.
Unfortunately, WebSocket only comes with flaws. Cross-Site WebSocket Hijacking (CSWSH) is a security threat that allows malicious actors to hijack a legitimate WebSocket connection, allowing them to intercept, modify, delete, and inject data. They are also vulnerable to Denial-of-Service attacks, which can prevent legitimate users from accessing the network. WebSocket can also perform man-in-the-middle attacks, allowing attackers to modify or inject data into the network without the user’s knowledge.
Here’s everything you need to know about WebSocket!
What is WebSocket?
WebSocket allows two-way communication between a website and its server in real-time. It is a protocol that allows the client and server to transmit messages over the channel at the same time. They’re used for things like chat apps and updating information on a website without having to refresh the page.
The WebSocket-based connection lasts as long as either party lays it off. When one party terminates the connection, the second party can no longer communicate since the link is automatically terminated.
WebSocket, like HTTP, can be either encrypted or unencrypted, as defined by the WebSocket schemes ws and wss, where ws:// is an unencrypted WebSocket, and wss:// is an encrypted WebSocket over TLS.
They act as a backdoor connection between your computer and the website. Instead of waiting for the website to send you information, you can ask for it and receive it immediately, and the website can also send you information without requiring you to refresh the page. It’s like a two-way phone call in which you and the website can converse simultaneously.
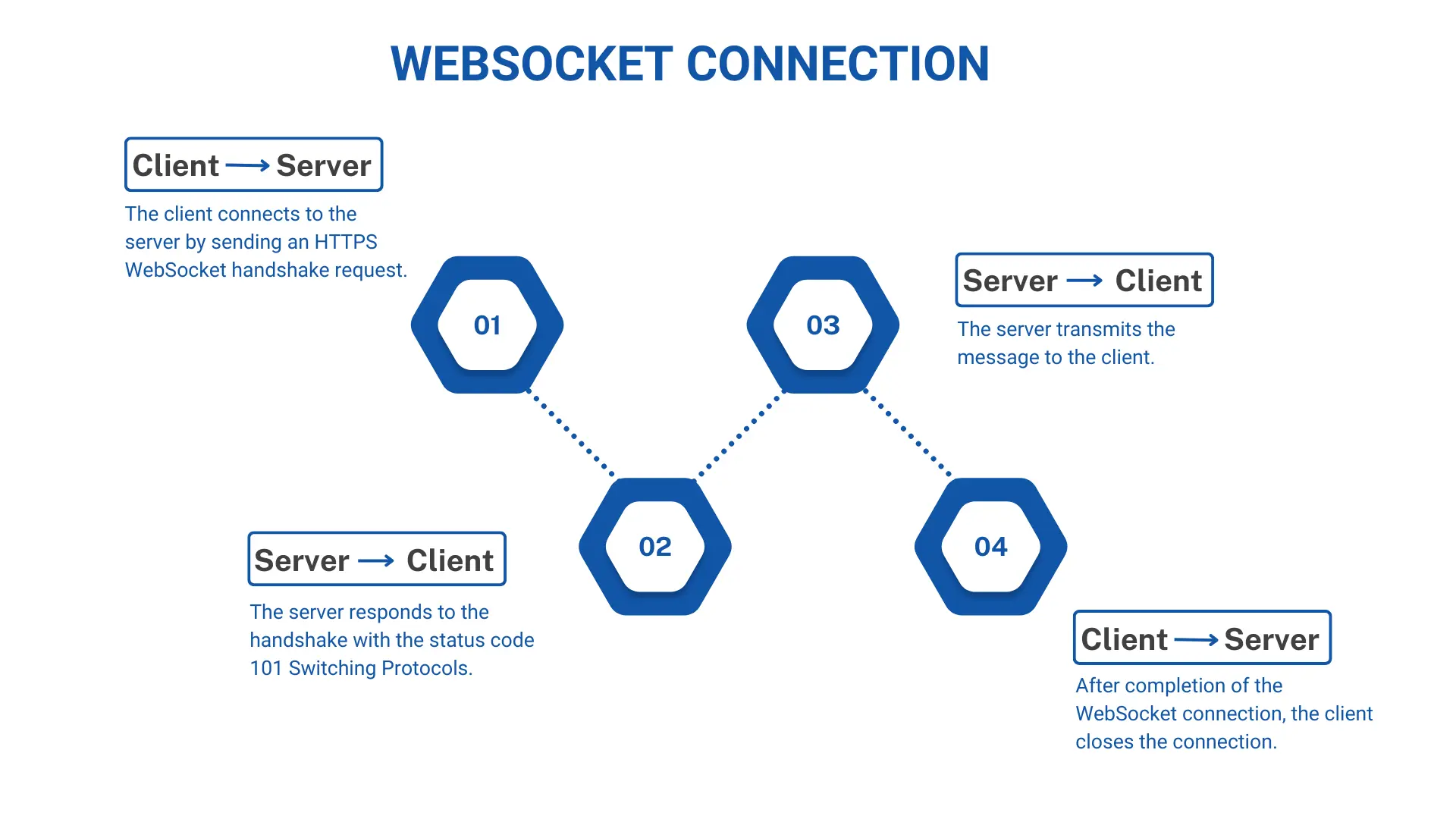
How Does WebSocket Work?
The usual WebSocket interaction between client and server consists of the following steps:
What are the Common WebSocket Vulnerabilities?
Improper WebSocket implementation can lead to serious vulnerabilities. Some of the most common security flaws are:
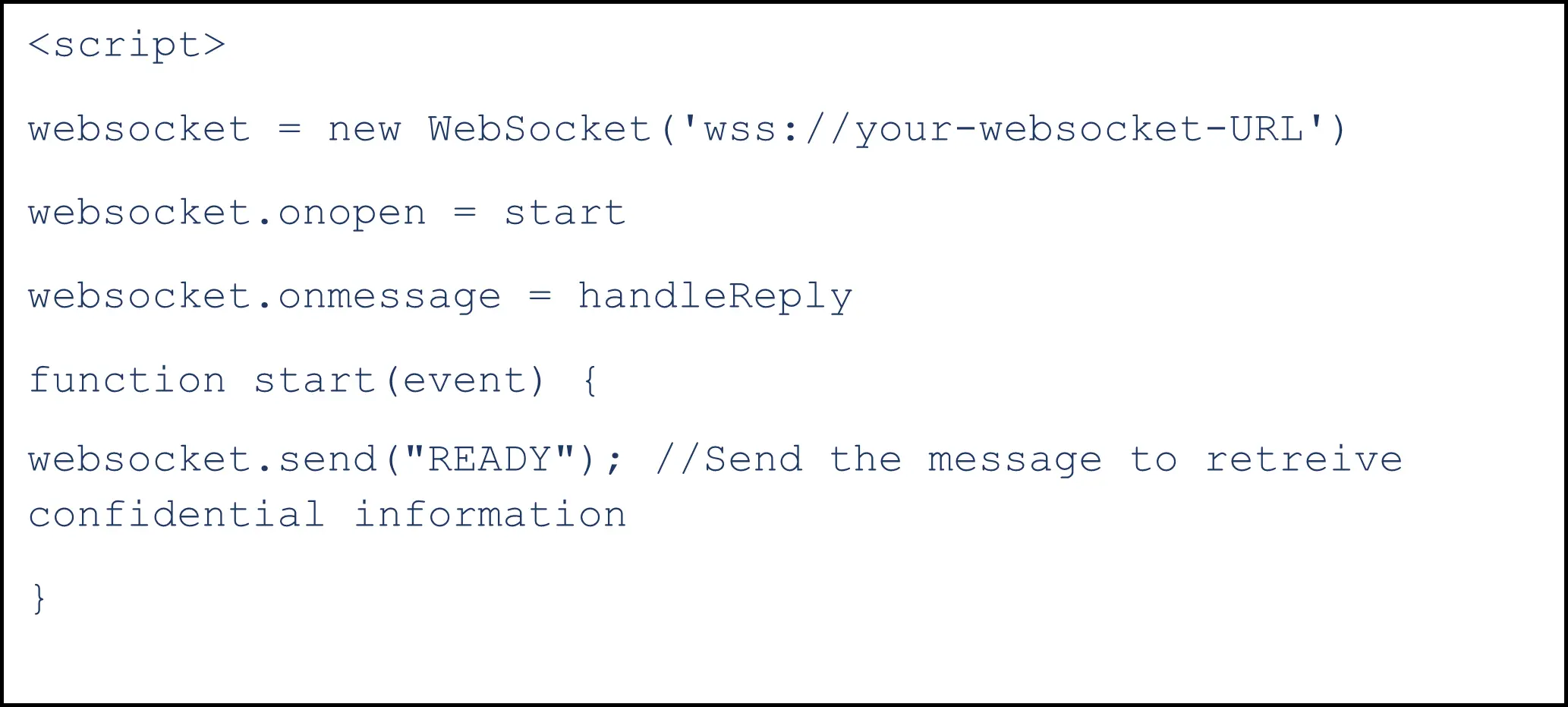
1. Cross-Site WebSocket Hijacking (CSRF with WebSockets)
If the WebSocket handshake relies on HTTP cookies for the session and does not include a Cross-Site Request Forgery (CSRF) token, an attacker can write a custom script on their domain to establish a cross-site WebSocket connection to the vulnerable application. Using this attack approach, an attacker might obtain sensitive information.
You can find a common script below that can be used to exploit this vulnerability:
2. Unencrypted Communications
A WebSocket, like HTTP, can be encrypted or unencrypted. It utilizes the WebSocket schemes ws and wss to differentiate between the two. In particular, ws:// represents an unencrypted WebSocket, whereas wss:// represents a WebSocket encrypted with Transport Layer Security (TLS).
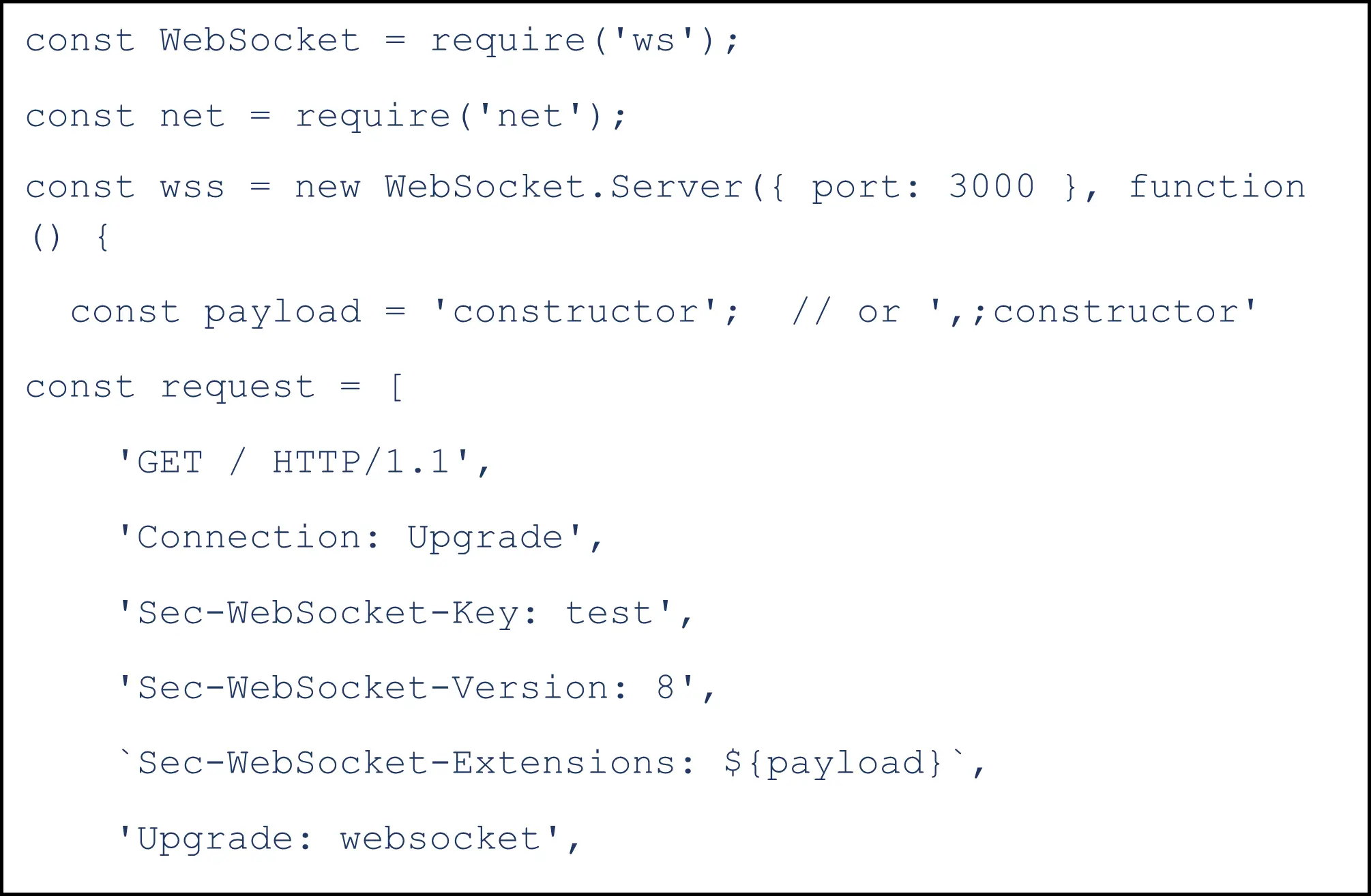
3. Denial of Service
The server may receive an endless number of connections via WebSocket. This allows an attacker to perform a denial-of-service attack against the server, which significantly strains the server and consumes all its resources, thus delaying communication.
The script below frequently crashes the WebSocket server, affecting some versions of the WebSocket client:
4. Sensitive Information Disclosure
This occurs when WebSocket fails to protect confidential information adequately and may allow unauthorized access to such information. Passwords, credit card information, private communications, and intellectual property are examples of sensitive data. Additionally, this type of security flaw can be vulnerable to various services and systems, including databases, operating systems, and network devices.
5. Input-Validation Vulnerabilities
If an attacker has access to WebSocket communications and the server does not properly validate or sanitize the input, an injection attack may occur. An attacker, for example, can deliver specially crafted payloads as messages while bypassing client-side validation by utilizing a proxy tool such as BurpSuite. Furthermore, attackers can launch attacks if the server does not validate the input for special characters or malicious data.
Let’s assume we’re testing a chat application that uses WebSocket. The system will transmit a message in the following format when a user types it:
In the absence of input validation, an attacker can intercept the request using a web proxy (Burp, in this example) to trigger an XSS pop-up by replacing their payload:

How Can you Ensure Your WebSocket is Safe?
You can use the following approach to avoid WebSocket Vulnerabilities:
• Make use of the wss:/ protocol (WebSockets over TLS).
• Hard code the URL of the WebSockets endpoint, and don’t include any user-controllable data.
• Avoid cross-site WebSocket hijacking vulnerabilities by protecting the WebSocket handshake message from CSRF.
• Avoid input-based vulnerabilities like SQL injection and cross-site scripting, and handle data properly on both the server and client sides.
Conclusion
The WebSocket industry is constantly evolving, and so are its security vulnerabilities. One thing to keep in mind is that not every WebSocket is vulnerable. However, if a WebSocket vulnerability is identified, address it immediately. Furthermore, organizations dealing with WebSocket must be extremely cautious and understand the need to implement all WebSocket security controls.
Accorian’s Pentesting Procedure
1. Data Collection
There are a variety of data collecting techniques, including Google Search, for acquiring data from a target system. In addition to web page source code analysis, various unrestricted tools and services are available on the market that gives information such as databases, table names, system software, and hardware used by third-party plugins.
2. Vulnerability Evaluation
Security flaws in the target network may be readily recognized based on the data acquired in the first stage. This allows penetration testers to perform attacks utilizing the system’s recognized entry points.
3. Practical Exploitation
Starting an assault on the target system is the most crucial phase, and it requires specialized expertise and procedures. Expert penetration testers may start an attack on a system using their talents.
4. Analysis of Results and Production of Reports
After conducting penetration testing, compile comprehensive reports for remedial measures. In these reports, all detected vulnerabilities and proposed remediation procedures are detailed. You may modify the format of vulnerability reports (XML, HTML, Microsoft Word, PDF) to meet the demands of your company.
The Accorian Advantage
In addition to penetration testing, Accorian can also recommend solutions or compensatory controls for identified vulnerabilities. Moreover, we can conduct penetration testing and map vulnerabilities to various compliance criteria to aid in prioritizing solutions. By doing so, we help customers understand the overall security posture of the environment.




