Being HITRUST-certified is one-way companies can demonstrate their commitment to security and privacy to clients and partners
Healthcare is one of the most highly regulated industries regarding privacy and security. There is a good reason for this, too, as personal health information (PHI) is some of the most valuable information for cybercriminals and people that commit fraud. According to the US Department of Health and Human Services 2020 Healthcare Breach Report, the average cost per breached record is $499 and can be sold for over $1000. As a result, PHI has become highly targeted by criminals, and to combat this, regulations and security standards have been created to ensure that businesses protect this information correctly. This article will discuss a popular security framework and certification in the healthcare industry called HITRUST.
What is HITRUST Certification?
HITRUST, created in 2007, is a standards and certification body that helps organizations manage information security, privacy, and regulatory compliance.
Organizations that achieve HITRUST certification have passed the framework checks and have shown an ability to adhere to the security requirements of HIPAA.
Then there is the HITRUST CSF framework.
What is HITRUST CSF
The HITRUST CSF is a certifiable security and privacy controls framework that provides organizations with a comprehensive, flexible, and efficient approach to regulatory compliance and risk management. Developed in collaboration with data protection professionals, the HITRUST CSF provides structure, transparency, guidance, and cross-references to 40+ authoritative sources, standardizing requirements and providing clarity and consistency. The HITRUST CSF is regularly updated as mapped authoritative sources change and new sources are introduced. Because the HITRUST CSF is both risk- and compliance-based, organizations of varying risk profiles can customize the security and privacy control baselines through various factors, including organization type, size, systems, and regulatory requirements.
The HITRUST CSF assurance program combines aspects of many popular security frameworks, including ISO, NIST, PCI, and HIPAA. So it’s not limited to just evaluating companies based on HIPAA requirements. There is a roadmap that organizations can follow to achieve data security and compliance with HIPAA.
Why is HITRUST Important in Healthcare?
Whether you are a healthcare provider or a processor of healthcare information, you have a big responsibility to ensure that you protect that information. Not only is this heavily mandated through regulations like HIPAA, but your potential clients will want to know that you can uphold these standards as part of their requirements for doing business with you. Being HITRUST certified is one-way companies can demonstrate their commitment to security and privacy to potential clients and business partners.
HITRUST vs. HIPAA
The relationship between HITRUST and HIPAA can be confusing at first. However, it’s essential to understand that they are not the same but are closely related. HIPAA stood for the Health Insurance Portability & Accountability Act and was passed by Congress in 1996. While HIPPA is a regulation created by lawmakers, HITRUST is a framework developed by security experts that covers key aspects of HIPAA compliance and draws from dozens of other authoritative sources, as well.
One of the issues organizations face with HIPAA compliance is translating somewhat vague requirements into quantifiable and measurable criteria and objectives. HITRUST helps companies achieve this by providing a framework for identifying the organization’s appropriate administrative, technical, and physical safeguards.
HITRUST Certification Requirements
Now that we’ve discussed the value of HITRUST in the healthcare industry, let’s look at how a company can become certified. For an organization to become HITRUST certified, it must undergo a validated assessment by a HITRUST assessor firm. The company must purchase a MyCSF subscription from HITRUST and a certification report credit. Upon completion of the validated review, the organization will submit the corrective action plans required for issues that were found. The assessor firm will, in turn, assess the company’s compliance with HITRUST CSF requirements and submit the assessment to HITRUST to spot-check the assessment results. If no significant problems are identified beyond what was found in the assessment, then the organization will be awarded HITRUST certification.
HITRUST Assessment Levels
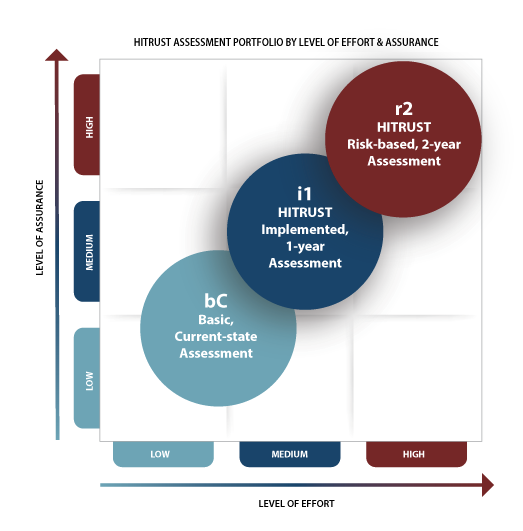
HITRUST offers three levels of assessments, basic, current-state assessment (bC), HITRUST Implemented, 1-year assessment (i1), and HITRUST risk-based, 2-year assessment.
Source @ HITRUST
HITRUST bC Assessment
This is the starting point for organizations seeking a HITRUST assessment. It is a standardized self-assessment that companies can perform without hiring an external assessor. It focuses on good hygiene and performs simple validations by applying HITRUST’s Intelligence Engine. The level of effort required is the lowest of all three, and it provides the lowest level of assurance and results in no HITRUST Certification.
HITRUST i1 Validated Assessment + Certification
This assessment is considered a validation of cybersecurity best practices and is well-suited for environments with moderate risk. HITRUST stated that this assessment would be threat-adaptive to reflect the evolving threat landscape and include a static list of required security controls. The level of effort required is considered moderate by HITRUST, but it gives a good level of assurance and allows you to get a one-year certification by HITRUST. The i1 assessment must be completed annually or replaced by an r2 Validated Assessment on or before the anniversary of the i1 submission.
HITRUST r2 Validated Assessment + Certification
This fully tailored assessment considers multiple risk factors relevant to the company that is undergoing the assessment to determine its scope. The r2 is most suitable for high-risk scenarios where high-level assurance is required or expected. When an external assessor completes this, it results in a two-year certification for HITRUST as opposed to 1 year under i1.
What is HITRUST MyCSF?
The MyCSF tool is a SaaS platform that helps organizations navigate and prepare for the HITRUST assessment process. It allows organizations to manage information risk and meet international, federal, and state regulations around privacy and security. It also helps organizations understand the gaps between their current state and international standards and best practices. Some of its key features include:
MyCSF Compliance and Reporting Pack for HIPAA:
The tool automatically compiles the list of evidence collected from your HITRUST assessment process and provides recommendations on what is required to ensure HIPAA compliance. The information from your assessments is consolidated into a report formatted by HIPAA control and populated with evidence that can be shared directly with the Office for Civil Rights (OCR) investigators.
Custom Assessments:
It can tailor assessments to fit your organization’s needs by focusing on specific regulatory factors or specific control requirements individually.
Assurance Intelligence Engine:
This feature provides automated checks that evaluate our assessment documentation and flag potential errors that may slow down the assessment review process.
Recap
Healthcare is one of the most heavily regulated data security and privacy industries. This is why frameworks like HITRUST were created. HITRUST is not a regulation but a security framework and certification that demonstrates that the certified company adheres to security best practices, particularly the security requirements of HIPAA. Organizations that want to achieve HITRUST compliance must complete an i1 or r2 assessment by a HITRUST-certified external assessor. This certification allows other organizations to verify that this company has the proper security controls to protect PHI in their environment. The MyCSF tool is a SaaS platform that helps organizations govern risk and prepare for HITRUST assessment. If you want help getting your organization certified in HITRUST, you can book some time with one of our HITRUST experts here.